Best Practices for Secure Data Intake and Design
This file outlines best practices for secure data intake, modeling, and design. It highlights vulnerabilities in software that processes electronic data and offers solutions to mitigate risks. Users will learn from the SafeDocs Program to enhance their data handling strategies.
Edit, Download, and Sign the Best Practices for Secure Data Intake and Design
Form
eSign
Add Annotation
Share Form
How do I fill this out?
To fill out this document, first gather the necessary data according to the provided guidelines. Next, follow the structured approach outlined to ensure all required sections are completed. Finally, review and validate your entries before submission.
How to fill out the Best Practices for Secure Data Intake and Design?
1
Gather all necessary information and documentation.
2
Follow the structured guidelines provided in the document.
3
Complete all required sections thoroughly.
4
Review your entries for accuracy and completeness.
5
Submit the form as instructed.
Who needs the Best Practices for Secure Data Intake and Design?
1
Software developers need this file to understand secure coding practices.
2
Project managers require it for overseeing data integrity and security.
3
Data analysts utilize these guidelines to ensure accurate data processing.
4
Security specialists need it to identify potential vulnerabilities.
5
Compliance officers use it to ensure adherence to data handling regulations.
How PrintFriendly Works
At PrintFriendly.com, you can edit, sign, share, and download the Best Practices for Secure Data Intake and Design along with hundreds of thousands of other documents. Our platform helps you seamlessly edit PDFs and other documents online. You can edit our large library of pre-existing files and upload your own documents. Managing PDFs has never been easier.
Edit your Best Practices for Secure Data Intake and Design online.
Editing this PDF on PrintFriendly is easy and intuitive. Simply upload your document and begin making changes using our comprehensive editing tools. Save your edited copy for immediate download without hassle.
Add your legally-binding signature.
Signing the PDF on PrintFriendly is quick and convenient. You can sign the document electronically using our signature feature. Once completed, download your signed PDF immediately.
Share your form instantly.
Sharing your PDF on PrintFriendly is seamless. Utilize our sharing options to distribute your document via email or social media. Ensure your colleagues have access to the valuable information contained within your PDF.
How do I edit the Best Practices for Secure Data Intake and Design online?
Editing this PDF on PrintFriendly is easy and intuitive. Simply upload your document and begin making changes using our comprehensive editing tools. Save your edited copy for immediate download without hassle.
1
Upload the PDF document you wish to edit.
2
Use the editing tools to make the necessary changes.
3
Save your changes within the editor.
4
Review your edits for accuracy.
5
Download the final edited document.

What are the instructions for submitting this form?
To submit this form, complete all required fields accurately and thoroughly. After filling out the form, you may send it via email to submissions@domain.com or fax it to (123) 456-7890. Alternatively, physical submissions should be mailed to 123 Main St, Suite 100, City, State, ZIP.
What are the important dates for this form in 2024 and 2025?
For 2024 and 2025, important dates for submissions are as follows: Initial submission by March 30, 2024, with subsequent review periods on June 15, 2025. Deadlines for revision submissions are set for December 5, 2025.

What is the purpose of this form?
The purpose of this form is to provide structured guidelines for secure data handling practices. It aims to reduce vulnerabilities associated with electronic data intake and processing. By adhering to the outlined best practices, organizations can enhance their data security protocols.

Tell me about this form and its components and fields line-by-line.

- 1. Data Definition: Defines the types of data being processed.
- 2. Validation Rules: Specifies the criteria that must be met for data to be processed.
- 3. Dependencies: Lists any dependencies between data objects.
- 4. Authentication Details: Includes necessary credentials for data access.
- 5. Error Handling Instructions: Outlines how to address potential processing errors.
What happens if I fail to submit this form?
Failure to submit this form can lead to significant risks, including data mismanagement and security vulnerabilities. It is crucial to ensure that all sections are completed accurately to maintain operational integrity.
- Data Integrity Issues: Incomplete submissions may result in incorrect data handling.
- Security Vulnerabilities: Failure to provide proper data can lead to exploitation of weaknesses.
- Compliance Failures: Not adhering to submission guidelines may breach regulatory requirements.
How do I know when to use this form?

- 1. Data Collection: Utilize this form when gathering data from various sources.
- 2. Vulnerability Assessment: Employ it to evaluate potential weaknesses in data handling.
- 3. Compliance Verification: Reference the form to ensure alignment with regulatory standards.
Frequently Asked Questions
How can I edit this PDF?
Click on the upload button, select your PDF file, and use our editing tools to modify it as needed.
Is it possible to share this PDF?
Yes, you can easily share the PDF via email or social media directly from our platform.
Can I sign the PDF electronically?
Absolutely! Use our signature tool to add your electronic signature to the document.
What if I need to submit this form?
Make sure to fill it out completely, then submit it as instructed.
Can I download the edited PDF?
Yes, once you finish editing or signing, you can download your document.
What features does the PDF editor have?
Our PDF editor allows you to text edit, add images, and insert signatures easily.
Are there limits to what I can edit?
You can edit any text, images, or fields as long as they are not locked in the document.
Is there a user guide for this process?
A comprehensive guide is available on the website to assist you with editing and sharing.
What if I have technical difficulties?
Reach out to our support team for assistance with any issues you encounter.
Is there a cost associated with editing?
Editing PDFs on our platform is currently free of charge.
Related Documents - Secure Data Practices

Introduction to Controls in BeOS Programming - User Guide
This file provides an in-depth introduction to controls in BeOS programming. It includes explanations and examples of standard control types and how to handle messages from these controls. The document is essential for programmers looking to implement user input controls effectively.
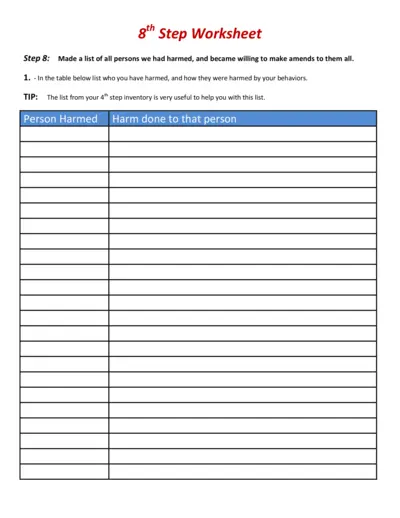
8th Step Worksheet: List and Willingness for Amends
This file is a worksheet for Step 8 in the recovery process, encouraging individuals to list persons they have harmed and become willing to make amends. It guides through listing those harmed, willingness to make amends, and includes prayers for strength and willingness. Use this worksheet to facilitate discussions with your sponsor.

Architecture Form Space and Order, Third Edition Ching
This file is an insightful guide into the principles of architecture, exploring the forms, spaces, and orders that define buildings. It is ideal for students and professionals in the field. The third edition includes enhanced content and a CD-ROM.

Information System Access Authorization and Briefing Form
This form is essential for accessing the classified information system. It includes instructions and responsibilities for users. Compliance is mandatory to prevent security breaches.

Vision Council 2022 Officers and Directors Slate
This document contains the 2022 official slate of officers and directors at large for The Vision Council. It includes the nomination details and the process for election during the annual business meeting. It lists candidates for officer and director positions, along with their terms.
Validated Templated Metadata Conversion using JSON and iRODS AVU
This document provides a methodology for bidirectional conversion of metadata between JSON and iRODS, validating and using templated metadata within the iRODS framework.

The Promises - Big Book of Alcoholics Anonymous
This file contains pages 83-84 of the Big Book of Alcoholics Anonymous, detailing 'The Promises' for those in recovery. It highlights the new freedom and happiness that can be achieved through the program. The content emphasizes personal transformation and spiritual growth.
How to Create Lazada Seller Account - Step by Step Guide
This file provides a comprehensive guide on how to quickly sign up for a Lazada seller account. It includes step-by-step instructions, useful tips, and important details about fees and charges. Ideal for aspiring e-commerce merchants.

Contract Quality Requirements and Responsibilities Manual
This file details quality assurance procedures and responsibilities according to part 46. It includes information on contractor and contracting office responsibilities. Requirements for various contract quality levels and procedures are also included.

The Ever-rotating Aspects of Function-Form-Meaning in Architecture
This paper presents a new triangular framework that integrates the main aspects of architecture: Function, Form, and Meaning. It discusses historical and contemporary theories, making the theories operational and applicable for further research. The framework helps interpret the relationships between different architectural aspects and aids in theoretical design.

State of North Dakota Purchasing Card Policy Agreement
This file contains the Purchasing Card Policy Manual Agreement for State employees of North Dakota. It includes terms of use, responsibilities, and procedures for the cardholders. Employees must comply with the stated provisions to avoid any penalties.

Data Subject Request for Personal Records
This file provides instructions for data subjects seeking access, correction, or deletion of personal records held by UC San Diego. It outlines the legal rights granted under GDPR and the California Information Practices Act. Users can fill out the request form for a timely response to their privacy inquiries.