Social Security Documents

Social Security
DCSA Open Storage Area Approval Checklist
This document is the DCSA Form 147, used to request approval for open storage areas under the National Industrial Security Program. It includes instructions and forms required for safeguarding classified information in such areas. This form is mandatory for contractors seeking approval for open storage of classified material.

Social Security
PCI Scan Vulnerability Report for Security Compliance
This file is a comprehensive PCI Scan Vulnerability Report. It contains details about the compliance status of various systems. Additionally, it outlines specific vulnerabilities detected during the scan.

Social Security
DSS Inspection Process: Proper Prior Planning & Preparation
This file provides comprehensive guidelines for DSS inspections, emphasizing the importance of proper prior planning and preparation. It includes instructions, essential steps, and tips for successful self-inspections. Ideal for individuals responsible for security inspections.

Social Security
Important Social Security Appeal Waiver Instructions
This document provides essential instructions regarding Social Security appeal waivers and repayment options. It details the rights against overpayment decisions and guidance for requesting reconsideration or waiver. Users will find relevant forms and contact information for assistance with the process.

Social Security
NIST Special Publication 800-167 Application Whitelisting
This document provides guidelines for implementing application whitelisting to enhance security. It offers best practices and methodologies for organizations. Ideal for IT professionals seeking to improve system security.

Social Security
Request for Change in Time/Place of Disability Hearing
This form is used to request a change in the time or place of a scheduled disability hearing. It is necessary for individuals who need to make adjustments due to circumstances that affect their ability to attend the hearing. Completing this form accurately will help facilitate the rescheduling process with the Social Security Administration.
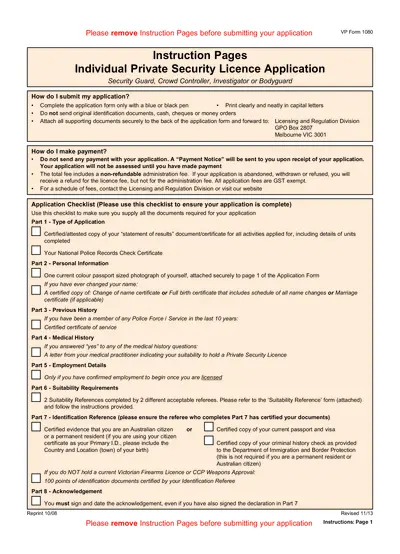
Social Security
Private Security Licence Application Instructions
This file provides detailed instructions for applying for a private security license, including application requirements and submission guidelines. It covers necessary documentation, payment information, and additional steps to ensure a complete application. Ideal for individuals seeking to enter the private security industry.

Social Security
Safeguarding Personally Identifiable Information
This document provides essential guidelines for safeguarding Personally Identifiable Information (PII) in both paper and electronic formats. It is a must-read for all U.S. Department of Homeland Security personnel and associates. Understanding how to handle PII securely is vital for protecting individual privacy.
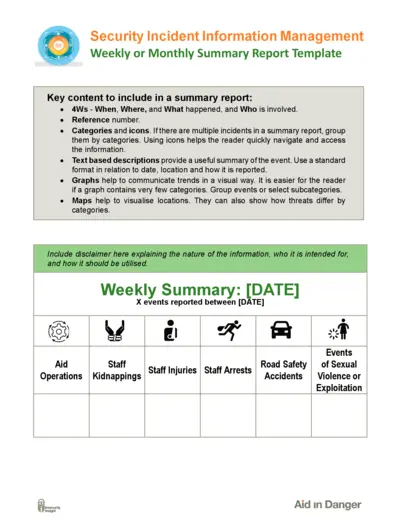
Social Security
Security Incident Information Management Summary Report
This file serves as a comprehensive template for creating security incident summary reports. It guides users on how to report incidents effectively and includes key trends and data visualizations. Ideal for those involved in incident management and reporting.
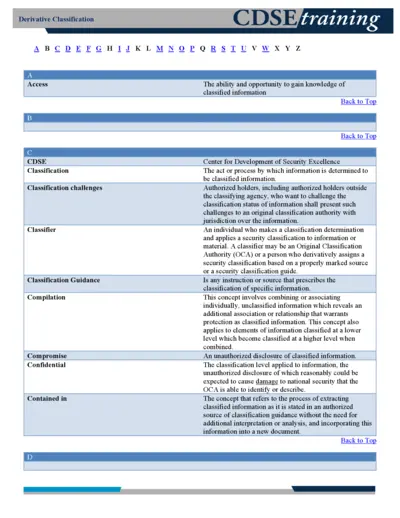
Social Security
Understanding Derivative Classification and CDSE Training
This file provides essential information about derivative classification and the standards set by the Center for Development of Security Excellence (CDSE). It outlines how to properly classify, protect, and downgrade sensitive information. Users will find valuable resources and guidance on handling classified data responsibly.

Social Security
Registration for Appointed Representative Services
This form is for registering for direct payment of fees. It's essential for appointed representatives needing to update their information. It also complies with IRS reporting requirements.

Social Security
Understanding Web Application Firewalls for Security
This document provides an introduction to Web Application Firewalls (WAFs) and their importance in securing online applications. It explains how WAFs work, the types of attacks they prevent, and the necessity for customization. Users will find valuable insights into implementing WAFs effectively for better security.